A VPC - virtual private cloud is a secure, isolated private cloud hosted within a public cloud. In VPC User can run code, store data, host websites, and do anything else.
Subnet — A range of IP addresses in your VPC.
Route table — A set of rules, called routes, that are used to determine where network traffic is directed.
Internet gateway — A gateway that you attach to your VPC to enable communication between resources in your VPC and the internet.
VPC endpoint — Enables you to privately connect your VPC to supported AWS services and VPC endpoint services. Instances in your VPC do not require public IP addresses to communicate with resources in the service.
Public Subnet - A public subnet is a subnet that is associated with a route table that has a route to an Internet gateway. This connects the VPC to the Internet and to other AWS services.
Private Subnet - A private subnet is a subnet that is associated with a route table that doesn’t have a route to an internet gateway. Instances in the private subnet does not have an internet access.
Step 1) Create new VPC
Create vpc >> write vpc name "my-pc" >> write IPv4 CIDR "10.0.0.0/16" >> create VPC
Usable Host IP Range : 10.0.0.1 - 10.0.255.254
Number of Usable Hosts : 65.534
Step 2) Create 2 subnet (one for public subnet and second for private subnet)
subnet >> create subnet >> select vpc >> write subnet name "public subnet" >> select Availability Zone >> write IPv4 CIDR "10.0.0.0/20" >> create subnet
Usable Host IP Range : 10.0.0.1 - 10.0.15.254
Number of Usable Hosts : 4,091
subnet >> create subnet >> select vpc >> write subnet name "private subnet" >> select Availability Zone >> write IPv4 CIDR "10.0.16.0/20" >> create subnet
Usable Host IP Range : 10.0.16.1 - 10.0.31.254
Number of Usable Hosts : 4,091
Step 3) Create Internet gateway and associate with vpc.
Internet gateway >> create Internet gateway >> write Internet gateway name "my-internet-gateway" >> create Internet gateway
Internet gateway >> select Internet gateway >> Action >> attach vpc >> select vpc >> Attach Internet gateway
Step 4) Create 2 route table (one for public route table and second for private route table)
route table >> create route table >> write route table name "private-route-table" >> select vpc >> create
route table >> select private-route-table >> subnet association >> edit subnet association >> select private subnet >> save
route table >> create route table >> write route table name "public-route-table" >> select vpc >> create
route table >> select public-route-table >> subnet association >> edit subnet association >> select public subnet >> save
route table >> select public-route-table >> Routes >> edit routes >> add route >> write "0.0.0.0/0" in destination section >> select internet gateway in target section >> save routes
Step 5) Create and configure NAT gateways(Network address translation)
NAT gateways >> Create NAT gateway >> write Name "my-nat-gateway" >> select public subnet >> allocate elistic ip >> create NAT gateway
Step 6) Assigne NAT gateway to private subnet (For accessing the internet in private ec2)
route table >> select private-route-table >> Routes >> edit routes >> add route >> write "0.0.0.0/0" in destination section >> select nat gateway in target section >> save routes
Step 7) Create new private ec2 instance
select VPC >> select private subnet >> select Auto-assign Public IP "disable"
note:- ssh , icmp port should be open.
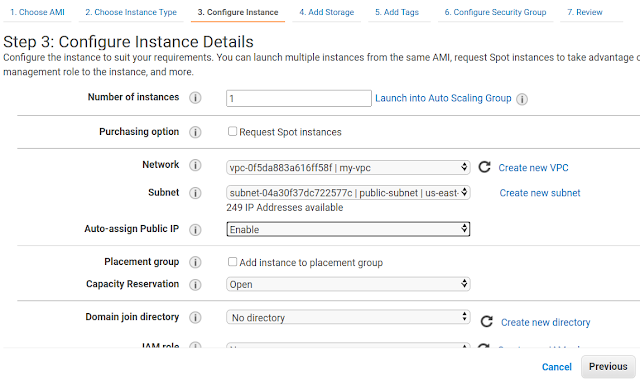
Step 8) Create public ec2 instance
select VPC >> select public subnet >> select Auto-assign Public IP "enable"
note:- ssh , icmp port should be open.
Step 9) connect ssh of public ec2 instance and ping private ec2 instance "private ip" or take ssh oh private ec2
Step 10) after taking ssh of private ec2 check google.com in pinging or not







No comments:
Post a Comment
testing